Cybersecurity plays a crucial role in ensuring the safety and security of autonomous vehicles and their systems. HoweverIn fact, there are numerous security challenges involved with autonomous driving poses a multitude of security challenges that should not be neglected under any circumstances.
Particularly in the area of cybersecurity Tthere are still many challenges to overcome, particularly in the area of cybersecurity, in order to enable the safe introduction and widespread use of autonomous driving. Autonomous driving, the ability of a vehicle to navigate without human intervention, has made tremendous progress in recent years.
SAE International classification of autonomous driving
SAE International’s classification provides To provide an overview of the development and current state of this technology, as well as SAE International’s classification provides a description of the different levels of autonomy in vehicles. From Level 0, where thea vehicle has no autonomous functions and is controlled by the driver, to Level 5, where thea vehicle can drive fully autonomously without human supervision, we have already seen impressive progress. PostAuto’s autonomous shuttle in Sion is just one example of many that illustrates the progressive development of autonomous driving and demonstrates the importance of cybersecurity for the safe use of this technology. However, there are still many challenges to overcome, especially in the area of cybersecurity, to enable the safe introduction and widespread use of autonomous vehicles.
The connected car is a complex system that interacts with a wide range of external services. As a result, it offers an attack surface comparable to modern IT systems.
Modern vehicles – a complex IT infrastructure with potential vulnerabilities
Cybersecurity plays a crucial role in ensuring the safety of vehicles and occupants, as autonomous driving and technology are closely linked. The level of connectivity in modern vehicles is extremely high and continues to increase. Basically, it is an extremely complex IT infrastructure that offers a multitude of potential attack surfaces and vulnerabilities. Therefore, the classic attack scenarios from the IT world can also be applied here, such as man-in-the-middle attacks, Trojans, and password attacks. A loss of data or control due to a hacker attack could have devastating effects on traffic safety.
Assessing functional security risks has long been a core element of automotive development. Cybersecurity risks are significantly more difficult to assess.
Differences between Functional Safety and Cybersecurity in Autonomous Driving
Functional Safety is based onrefers to the potential harmfulness of that can be caused by the technical system. It aims to reduce the risk posed bythat the system tocan impose on humans. Roughly speaking, Functional Safety deals with the effect of the system on humans. On the other hand, Cybersecurity looks at the impact of humans on the system and is therefore more difficult to assess than local Functional Safety.
In the case of car-to-x communication, cars are networked together to ensure safe distances, for example. However, a hacker could take control of a networked car and, for example, disable the safety measures. Our main topic arises from such a worst-case scenario: we need security measures to ensure the safety of modern vehicles in the future as well.
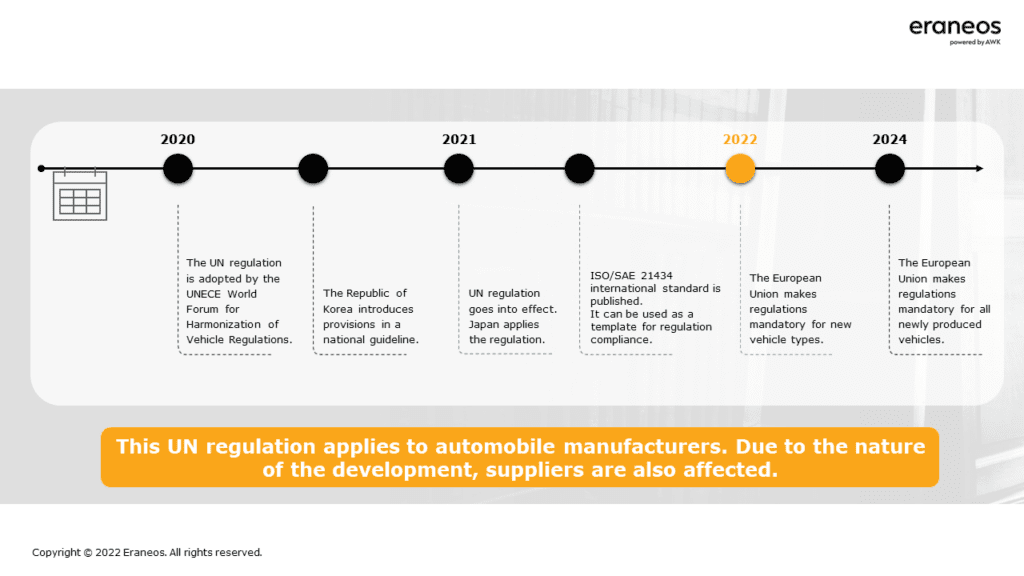
Cybersecurity in automobiles becomes an aspect of harmonized vehicle regulations and international standards
Harmonization and regulations can help reduce risks in autonomous vehicles. Since 2020, work has been underway on a UN harmonization regulation for motor vehicles, which in turn serves as the basis for the ISO/SAE 21434 standard currently in force. This standard stipulates, for example, that automotive manufacturers must manage their information security risks in a so-called CSMS (Cybersecurity Management System) and that they must audit their Tier 1 suppliers for compliance with the standards. From 2024, this standard will be mandatory in the European Union for all newly produced vehicles.
The top 5 measures for cybersecurity
All top risks must be addressed with concrete, measurable, and risk-reducing measures. We recommend the following top five measures:
1. Identify and actively manage risks
Risks should be analyzed, for example, through assessments or cyber-attack simulations that include vulnerability scans and penetration tests.
2. Actively manage information security
Integrating the issue of information security into the overall governance structure is key. Both aA security strategy and governance, including a continuous improvement process based on the PDCA cycle, help.
3. Actively manage OT security
The information security management system (ISMS) was not originally developed with operations technology (OT) or physical security in mind and should therefore be explicitly aligned and supplemented with them. Standards such as IEC 62443, which can be combined well with the ISO 27000 series, can help. They provide the necessary focus on the specific requirements for network and system security at the field, control, process control, operations control and enterprise levels. This is particularly important given the increasing IT capabilities of OT.
4. Extend IT and OT security to the supply chain
IT and OT security pose challenges for manufacturers, service providers, and operators along the entire supply chain. Increasing business integration requirements and capabilities, such as network connectivity and business logic, are countering the traditional network isolation approach. Each individual system is becoming increasingly complex. If a third party has a low maturity level or is not sufficiently secured, this opens – figuratively speaking – many doors and windows, whereby the entire ecosystem can and will be attacked.
The ISO 27000 series is well focused on organizational and process aspects, while IEC 62443 also contains technical proposals for incorporating security aspects into the entire supply chain of modern OT infrastructures. These must already be anchored in the contracts.
5. Addressing top risks with concrete measures
The first four measures clearly result in implementation plans that require concrete action. These can range from (awareness) training of employees on current threats and security issues or phishing campaigns to backup concepts, where it is important that the importing and restoring as well as the subsequent use of a backup is tested and practiced.