The Challenge
Critical infrastructure is the target of cyber attacks worldwide. Our client’s goal was to implement an advanced security framework to protect both the supply chain and the IT environment. Traditional perimeter security is increasingly outdated, so there was an ambition to establish a Zero Trust strategy. Every access point and communication within the infrastructure is continuously verified to secure sensitive processes and prevent potential breaches. In doing so, this organization, like the rest of the industry, is facing legislation that will be radically renewed next year. They currently fall under the Wbni, and with the Cybersecurity Act (based on NIS2 Directive) in the pipeline, many vital companies need to step up their efforts. Naturally, Eraneos has risen to this “never trust, always verify” challenge.
The Approach
The organization sought guidance in effectively applying Zero Trust principles within their IT infrastructure, focusing on key areas such as identity management, network segmentation and endpoint security. Eraneos was engaged because of its professionalism and people-oriented approach. To make Zero Trust applicable to the specific characteristics of the organization, intensive workshops were held with internal stakeholders to determine the definition of Zero Trust for the unique operating environment. These sessions revealed that there were varying interpretations of Zero Trust, highlighting the importance of establishing clear and unambiguous principles.
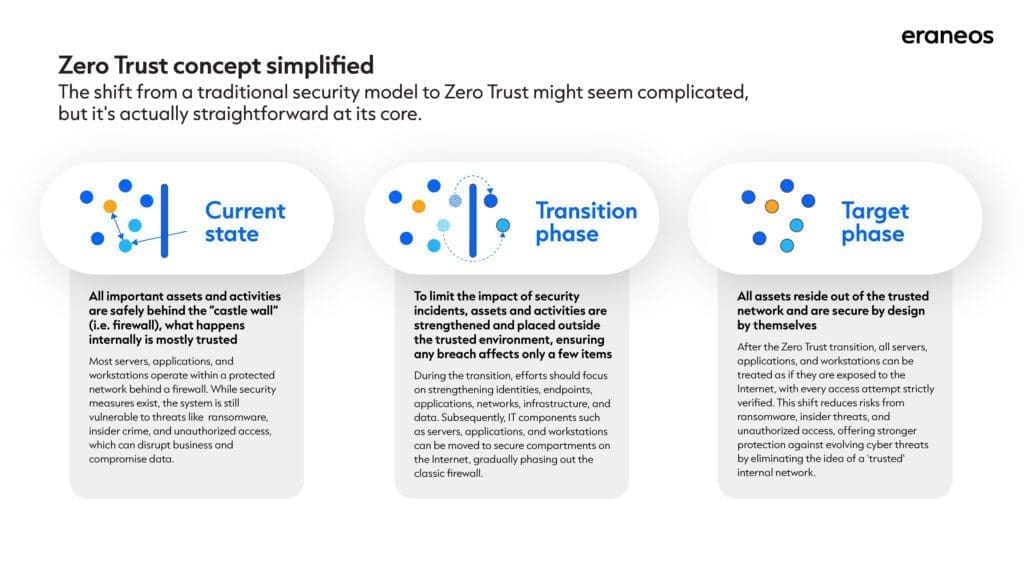
A customized Zero Trust strategy was developed, based on a widely used maturity model that breaks down the approach into six key areas:
- Identities – Specific roles and responsibilities combined with strict authentication via multi-factor authentication (MFA) for all users.
- Endpoints – Make all devices more resilient and remove them from the corporate network, so there is limited impact in the event of a cyber incident.
- Applications – Isolate applications to ensure that each application functions as a secure, self-contained island.
- Network – Moving away from the traditional firewall model by adopting microsegmentation, where each network segment becomes an independent secure entity.
- Infrastructure – Reconfiguring servers and other critical systems into independently secure components.
- Data – Apply advanced access controls to ensure that employees have only temporary or role-based access to specific data elements, rather than full access to all information.
This Zero Trust approach places a strong emphasis on authentication, where no access, action or device is trusted by default, even within the company’s internal network. To manage this shift, the current state of security practices was mapped and measured against a target state with specific milestones and ongoing assessments.
The Zero Trust model is further supported by automation. The traditional approach requires manual interventions, but modern automated systems respond immediately to threats. This minimizes downtime and significantly reduces the risk of major disruptions in the event of a cyberattack.
The Result
The Zero Trust framework enables customers to modernize their security posture and strengthen defenses. Key quick fixes, such as security measures within the supply chain and strengthening individual endpoints, are implemented early with minimal disruption to ongoing operations. More impactful actions, such as a complete network architecture overhaul, are planned in a phased approach, allowing the business to transition smoothly without interrupting operational continuity. Because the framework is designed together with the customer, it does not just remain a plan.
As a result, the organization will soon be operating with much greater confidence in their security, in line with the upcoming implementation of the Cybersecurity Act (Cbw) that includes more stringent requirements for risk management and critical infrastructure security.
With Zero Trust principles firmly embedded in their strategy, the company will soon be able to manage risk more effectively and adapt more quickly to future threats.
Although challenging, the first steps toward a Zero Trust transition have been taken. The direction has been set and now it is time for the implementation phase, allowing this international organization to maintain its leading position. This transformation ensures that the security of both the supply chain and the IT environment are optimally supported, according to Zero Trust principles.