Q-Day Is Upon Us In Five Years’, Or Even Sooner…
The term “Q-Day” refers to the day when quantum computers will have the capability to break today’s widely used encryption methods. Like the Y2K event, Q-Day presents a looming technological challenge that requires immediate attention from organizations worldwide. The Australian Signals Directorate (ASD) has predicted that Q-Day will likely occur soon after 2030. If this prediction holds true, businesses have just five years to prepare their infrastructure to withstand the disruptions posed by quantum computing.
While quantum computing brings transformative benefits across various sectors, it also introduces significant risks to data security. The primary threat is to the confidentiality and integrity of critical business data, as quantum computers will be capable of breaking encryption standards that have been reliable for over two decades.
Understanding The Impact Of Q-Day
Q-Day is not just a theoretical concern—it represents a significant shift in cybersecurity. Once quantum computers surpass classical computing capabilities, they will render many of today’s encryption algorithms obsolete. This poses risks across industries, including finance, healthcare, logistics, and government sectors, where sensitive information is frequently transmitted and stored.
The ASD’s warning underscores the urgency for businesses to act now. Organizations must transition to quantum-resistant encryption methods to protect their data from future threats. Failing to do so could result in compromised security, loss of trust, and regulatory repercussions.
Preparing for Q-Day: Steps Organizations Should Take
To prepare for the post-quantum era, every organization needs to ensure that they build an inventory of every encryption solution across their digital infrastructure and then build a plan for updating the encryption to meet Post Quantum Encryption Standards.. We at Eraneos identified five future dimensions to cover as follows:
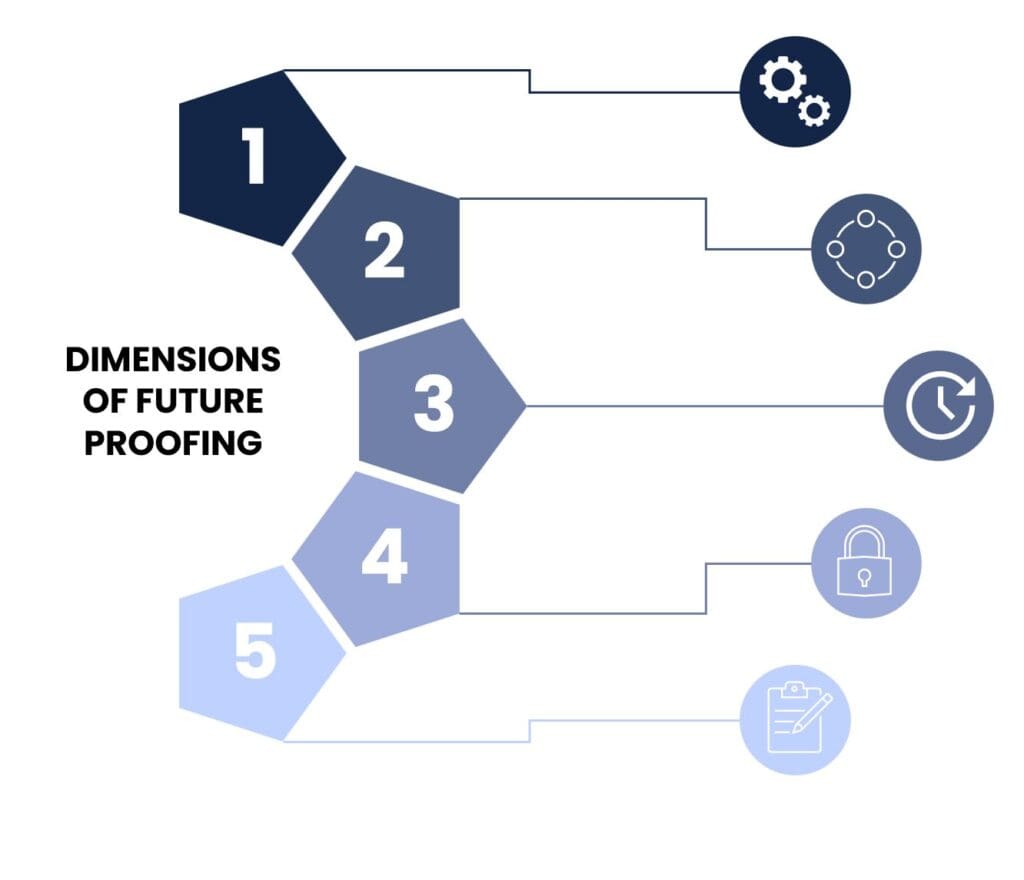
- Hybrid Cryptography Implementations: Implement hybrid cryptography, where classical and quantum-resistant algorithms are combined, allowing a gradual transition while maintaining security.
- Algorithm Agility: Design PKI systems with algorithm agility, allowing seamless switching to new cryptographic algorithms as standards evolve.
- Data Longevity Considerations: Data Longevity Considerations: Under DORA, organizations must ensure that their IT infrastructure is not only functional but also robust so that it can withstand external risks. This goes beyond traditional measures such as firewalls and antivirus programs; it requires layered security that also takes into account vulnerabilities in the chain. This means that not only the suppliers, but also fincnial institutions themselves must take measures to ensure continuity of critical services in the event of supplier failure.
- Secure Key Management and Storage: Update key management protocols to support PQC, including methods for securely generating, storing, and revoking quantum-safe keys.
- Regular Compliance and Security Assessments: Establish a regular schedule for security audits and compliance checks, aligned with evolving PQC standards from NIST and other bodies.
The Role of Eraneos Group in Preparing for Q-Day
At Eraneos Group, we understand the complexities and challenges associated with transitioning to post-quantum encryption. With many business leaders already focused on navigating the impact of AI, it’s crucial to prioritize encryption upgrades to mitigate future risks. Here’s how we can help:
- Risk Assessment: We conduct comprehensive risk assessments to identify vulnerabilities in your current encryption infrastructure.
- Strategy Development: Our experts will help you develop a tailored strategy to transition to post-quantum cryptography.
- Implementation Support: We provide hands-on support to implement new encryption solutions and ensure a smooth transition.
- Training and Upskilling: We offer training programs to bridge the skills gap, ensuring your teams are prepared for the post-quantum era.
The Countdown to Q-Day: Why Act Now?
While the exact date of Q-Day remains uncertain, the window for preparation is rapidly closing. The publication of cryptography guidelines by the Australian Signals Directorate highlights the importance of taking action now. Organizations should aim to complete their transition to post-quantum encryption by 2030 to safeguard their digital assets against future quantum threats.
Business Leaders Must Start Planning Today to:
- Ensure regulatory compliance
- Maintain customer trust
- Protect sensitive information
- Minimize business disruptions
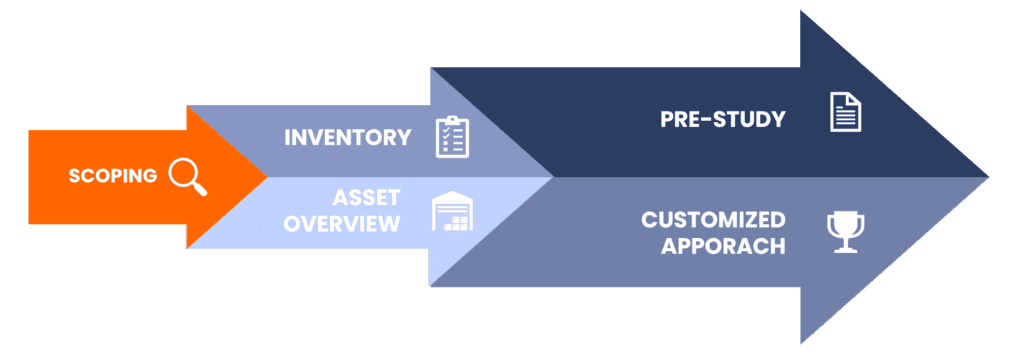
The Eraneos Approach of Q-Day
Find your strategy
- Status indicator for PQC readiness of current PKI based on best practices (procedures, key management, implementation practices, key creation).
Asset overview
- Categorised and prioritised asset overview, enhanced with live data from network traffic.
- Analyses of compatibility with new cryptographic keys.
- Prioritisation of systems and risk analyses.
Pre-study
- Implementation strategy based on current PKI system.
- Adjusted key integration and revocation process for quantum resistant keys.
- Risk management concept for PKI.
- Security revies concept and Disaster recovery and backup concept.
In conclusion, the rise of quantum computing presents both opportunities and risks. By taking proactive steps to transition to post-quantum cryptography, organizations can mitigate future security threats and ensure continued resilience in an increasingly digital landscape. At Eraneos Group, we are committed to helping businesses navigate this transition and secure their data for the future. Contact us today to learn more about how we can assist you in preparing for the post-quantum era.

Carlo Gebhardt
Partner