Executive Summary
Cryptography is ubiquitous across every IT system. It serves to protect data, authenticate users, or guarantee the integrity of communications for every component: application, server, data centre, cloud, endpoint, and mobile device.
As quantum computing progresses from theoretical to practical, the threat to classic cryptography accelerates. Widely used public-key cryptographic systems like RSA and ECC are projected to become insecure once quantum computers are large and reliable enough. In response, regulators such as the EU are mandating organizational transition plans for post-quantum cryptography (PQC) by 2026 and implementation in high-risk areas by 2030.
To address this, organizations must adopt crypto-agility, the organizational capability to rapidly adapt cryptographic systems and protocols with minimal operational disruption. Crypto-agility provides the flexibility to cope with uncertainty around PQC standards and evolving quantum or classical threats.
This article provides a comprehensive overview of key requirements for building crypto-agility, enabling organizations to maintain long-term security, regulatory compliance, and resilience.
Why should organizations be concerned with the transition to post-quantum cryptography?
The European Union’s mandate for organizations to prepare post-quantum cryptography (PQC) transition plans by 2026 is significant due to the pervasive role cryptography plays as the cornerstone of digital trust. Cryptography is far from being limited to specific and isolated use cases – such as encrypting hard drives. In fact, cryptography runs deeply into organizations’ business and IT operations, permeating every single aspect of digitalization. It secures communications (TLS, VPNs), enforces identity and access (digital certificates, authentication protocols), supports business processes (payments, code signing, secure document exchange, e-invoicing), and protects emerging technologies such as blockchain and IoT.
In other words, the urgency of transitioning from current to post-quantum cryptography does not only stem from the threat of quantum computing itself, but also from the scale of its impact. Given this ubiquity, the transition to PQC cannot be approached as a simple replacement of algorithms; instead, it requires comprehensive planning and coordination across the organization.
Advances in quantum computing and the threat to today’s cryptography
Why is quantum computing such a threat to current cryptography?
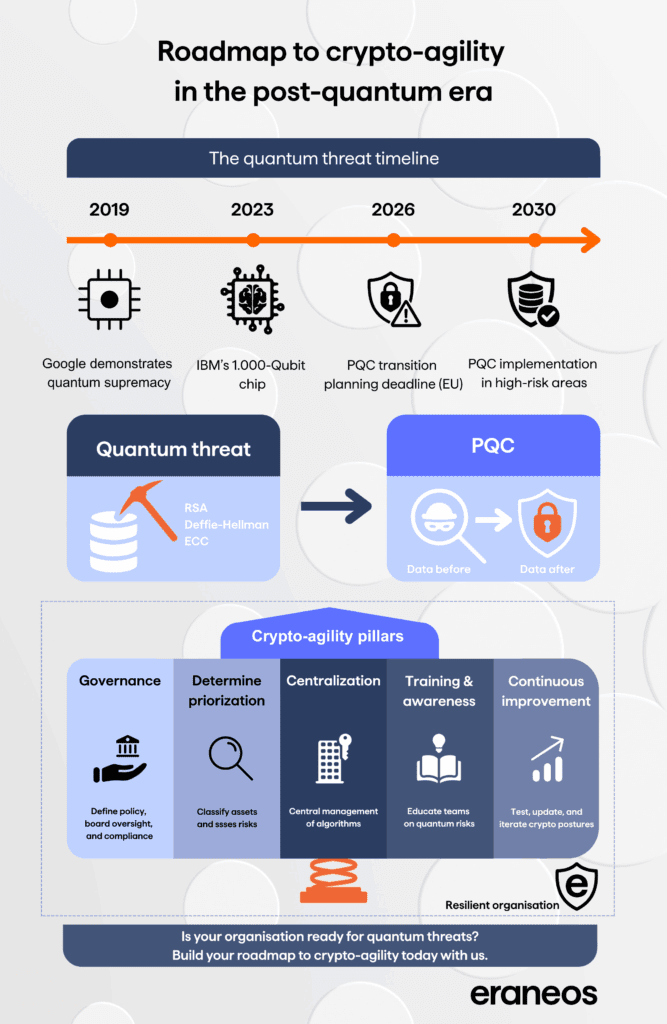
For decades, quantum computing has been viewed as a distant, hypothetical threat, always “ten to twenty years away.” But recent breakthroughs are rapidly reshaping that outlook. Events such as Google’s 2019 quantum supremacy demonstration, IBM’s unveiling of its 1,000-qubit Condor chip in 2023, and China’s progress in superconducting qubits all highlight the accelerating pace of quantum research. As the likelihood of a large-scale and stable-enough quantum computer grows, so does the urgency for institutions to prepare.
Large and stable quantum computers running Shor’s algorithm will render staple public-key cryptographic systems, RSA, ECC, and Diffie-Hellman, obsolete. These algorithms form the backbone of data protection, identity verification, and trust in digital processes. A sufficiently powerful quantum machine would compromise even currently secure communications, putting data at risk retroactively through “harvest now, decrypt later” attacks.
Regulatory focus:
Recognizing the stakes, governments and regulators are taking proactive steps. The European Union, for instance, has mandated that organizations define transition plans to PQC by the end of 2026 (EU reinforces its cybersecurity with post-quantum cryptography | Shaping Europe’s digital future), with implementation required in high-risk areas by 2030. Australia and others have set similar timelines (Guidelines for cryptography). The clear message: the time to act is now.
Past transitions show that proactive cryptographic overhaul is possible. For example, migrating from the Data Encryption Standard (DES) to the Advanced Encryption Standard (AES) of the early 2000s, prompted by DES’s inability to withstand brute-force attacks, demonstrated that staying ahead of evolving threats and adapting security infrastructure is both necessary and possible.
However:
Even as organizations move toward PQC, the transition will not be a one-time event. The algorithms proposed for the post-quantum era are still evolving and, in many cases, unproven at scale. For example, SIKE, once considered a leading PQC candidate, was cracked in under an hour on a classical laptop. Similar questions about long-term reliability surround NTRUEncrypt and others.
Key point:
Organizations must prepare for a journey of ongoing cryptographic transitions, defined by continuous evolution, emerging vulnerabilities, and accelerating change.
Crypto-agility: Turning post-quantum migration into the foundation for continuous cryptographic resilience
Why is becoming “crypto-agile” essential, and how does it differ from prior migrations?
While regulatory mandates, such as those issued by the EU, compel organizations to transition toward post-quantum cryptography (PQC), this transition represents far more than just another periodic technical upgrade. In today’s complex, interdependent digital world, reactive, one-off migrations are too risky and disruptive.
Proactive, organizational crypto-agility means operationalizing the capacity to continuously adapt, upgrade, and evolve cryptographic systems without major disruption. Instead of simply replacing vulnerable algorithms, crypto-agility embeds this adaptive ability into governance, architecture, operations, and vendor management.
This article structures crypto-agility around the five following foundational pillars:
1. Governance first: How does leadership shape lasting cryptographic resilience?
The foundation of any successful transformation lies in robust, visible governance. This means:
- Securing full endorsement from board and executive leadership, backed by budget, accountable teams, and clear KPIs.
- Aligning cryptography policies with all relevant regulations, such as the EU’s Cyber Resilience Act (CRA), NIS2 Directive, and the EU’s PQC roadmap.
- Defining and enforcing approved cryptographic algorithms and protocols, including phase-out of deprecated standards and creating clear internal controls.
Communicating updated governance internally, to create both structural clarity and the cultural support required for crypto-agility.
2. Laying the technical ground: What steps enable technical crypto-agility?
With a governance in place, a technical roadmap becomes the next block to tackle. Unfortunately, the deep rooting of cryptography within the IT environment causes this roadmap to require profond investigations that are embodied in the 4 steps below:
- Conduct full cryptographic discovery: Identify where all cryptography is used across the organization, therefore building a complete inventory of algorithms, key lengths, protocols, libraries, and key management systems. To guide this effort, focus on three key layers:
- Infrastructure & Data Security (TLS, VPNs, encrypted storage/backups, cloud)
- Identity & Access Management (SSH keys, X.509 certificates, SAML/OIDC, PKI)
- Business Processes (code signing, secure document exchange, digital signatures, e-invoicing)
- Map all cryptographic usage to the specific data types it protects: By understanding which data type is transmitted or stored through each channel, one can determine how that data is currently being secured.
- Perform threat modeling and risk assessment: Based on the mapping, evaluate exposure, business impact, and quantum-era threats (like “harvest now, decrypt later”).
- Develop a prioritized, risk-aligned transformation plan that identifies both urgent replacements and lower-risk, longer-term transitions.
3. Centralization: Why is centralized control crucial for crypto-agility?
Centralized control points are key to crypto-agility, as they provide a single source of truth, streamline standards enforcement, and enable rapid adaptation when cryptographic algorithms or regulations change. Implementation typically involves the following steps:
- Implement a robust Key Management System (KMS) to orchestrate key generation, rotation, revocation, and decommissioning across the full key lifecycle.
- Standardize cryptographic libraries for in-house development: Require all software teams to use a single, vetted, approved cryptographic library, avoiding ad-hoc or legacy implementations.
- Enforce cryptographic requirements and expectations with vendors and third parties via contract clauses, due diligence, and regular compliance checks.
- Consolidate controls across infrastructure, applications, and external dependencies to enable rapid and coherent response to new threats or standards.
4. Enabling cultural shift through training & awareness: How can organizations build crypto-agility into their culture?
Despite all technical works, culture is the cornerstone for adoption. That is, one has to ensure that intentions are clear, goals are set, and skills are taught. For that, the following actions need to be taken:
- Run internal communication campaigns about quantum risks and the importance of crypto-agility.
- Mandate tailored training:
- Developers: Secure use of vetted libraries
- IT/security teams: System configuration and enforcement
- Procurement/legal/app owners: Supplier evaluation and integration of cryptographic requirements
- Invest in organization-wide education so that crypto-agility becomes part of standard operations, not just a one-off initiative.
5. Continuous improvement: How do you sustain crypto-agility?
Last but not least, continuous improvements are key to sustainability. Therefore, it is key that the following actions are undertaken and lived:
- Periodically refresh inventories and reassess risk as algorithms, threats, and regulations evolve.
- Build feedback mechanisms and flexible change-management processes to allow rapid adoption of new cryptographic standards.
- Monitor for emerging quantum and classical risks so your cryptographic estate can be adapted before vulnerabilities become critical.
Conclusion: From quantum readiness to lasting agility
While regulations like the EU’s roadmap call for PQC adoption by 2030, sustained security and trust demand more than compliance.
Now is the time for organizations to build true crypto-agility: the ability to anticipate, adapt, and respond quickly, securely, and seamlessly to cryptographic challenges as they arise. This ensures sensitive data is protected, not just against quantum threats, but in the face of all future innovations and risks, greatly reducing the business impact and operational disruption of the next migration.
FAQ
Q: What is crypto-agility and why does it matter?
A: Crypto-agility is the ability to quickly adapt cryptographic systems and standards as threats and technologies change. This is vital for resilience in the post-quantum era.
Q: What are the EU PQC compliance deadlines?
A: Draft plans by end of 2026; implementation in high-risk areas by 2030.
Q: What’s the first step organizations should take?
A: Conduct a comprehensive inventory of all cryptographic usage and map it to systems and business risk.